Understanding Multi-Factor Authentication (MFA) and How It Works
Multi-factor authentication (MFA) is a security feature that helps protect online accounts by requiring multiple forms of verification before granting access. Instead of relying solely on a password, MFA adds extra layers of security to ensure that only the rightful owner can log in.
How Multi-Factor Authentication Works
When logging into an account with MFA enabled, users must provide at least two of the following verification factors:
- Something You Know – A password or PIN.
- Something You Have – A mobile phone, authentication app, or security key.
- Something You Are – Biometric verification such as a fingerprint or facial recognition.

For example, if you enter your password (something you know), you may also be asked to enter a one-time code sent to your phone (something you have). This extra step significantly reduces the risk of unauthorized access.
Why Multi-Factor Authentication is Crucial for Online Security
Cyber threats are more advanced than ever, and relying on just a password is no longer enough to protect your online accounts. Multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for hackers to gain unauthorized access.
How Multi-Factor Authentication Enhances Security
- Protects Against Stolen Passwords
Many people reuse passwords across multiple sites. If a hacker steals your password from one account, they can easily access others. MFA prevents this by requiring additional verification. - Reduces the Risk of Phishing Attacks
Phishing emails trick users into revealing their login credentials. Even if an attacker obtains your password, they still need a second authentication factor to access your account. - Stops Unauthorized Logins from Unknown Devices
MFA ensures that even if someone gets your password, they won’t be able to log in from a new device unless they verify their identity through a second factor. - Adds an Extra Layer of Protection for Sensitive Data
Businesses, banks, and government institutions require MFA to safeguard confidential information. It helps prevent unauthorized access to financial records, emails, and personal data.

Common Types of Multi-Factor Authentication Methods
With the rise of cyber threats, multi-factor authentication (MFA) has become a crucial security feature for protecting online accounts. MFA requires users to verify their identity using multiple authentication factors, making it much harder for hackers to gain access. Here are the most common types of MFA methods used today.
1. One-Time Passwords (OTP)
One-time passwords (OTP) are temporary codes sent via SMS, email, or authentication apps. These codes are valid for a short period and must be entered along with the primary password.
✅ Pros: Easy to use, widely supported.
❌ Cons: SMS-based OTPs can be intercepted by hackers using SIM swapping.
2. Authenticator Apps
Apps like Google Authenticator and Microsoft Authenticator generate time-sensitive codes that users enter when logging in. These apps work even without an internet connection, making them more secure than SMS-based OTPs.
✅ Pros: More secure than SMS, works offline.
❌ Cons: If you lose your phone, you may need backup codes to regain access.
3. Biometric Authentication
This method uses unique biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify identity. Many smartphones and laptops support biometric authentication for secure logins.
✅ Pros: Quick and highly secure.
❌ Cons: Some biometric systems can be fooled by high-quality images or deepfake technology.
4. Security Keys
A physical security key (such as a YubiKey) is a USB or NFC device that users insert or tap to authenticate their login. Security keys offer the highest level of protection against phishing attacks.
✅ Pros: Extremely secure, resistant to phishing.
❌ Cons: Requires carrying a physical key, which can be lost.
5. Push Notifications
Push-based authentication sends a login approval request to a trusted device. Users simply tap “Approve” or “Deny” to complete the authentication process.
✅ Pros: Easy and fast, prevents phishing attacks.
❌ Cons: Requires internet access on the trusted device.
6. Email-Based Verification
Some services send an email verification link when an unusual login attempt is detected. The user must click the link to confirm their identity.
✅ Pros: Simple and convenient.
❌ Cons: If an attacker gains access to your email, they can bypass MFA.
Final Thoughts
Each multi-factor authentication (MFA) method has its strengths and weaknesses. The best approach is to use a combination of methods to maximize security. For most users, an authenticator app or security key provides the best balance of convenience and protection.
How to Set Up Multi-Factor Authentication for Better Protection
Enabling multi-factor authentication (MFA) is one of the most effective ways to enhance your online security. It adds an extra layer of protection, ensuring that even if someone steals your password, they still need an additional verification factor to access your account. Below is a step-by-step guide on how to set up MFA for better protection.
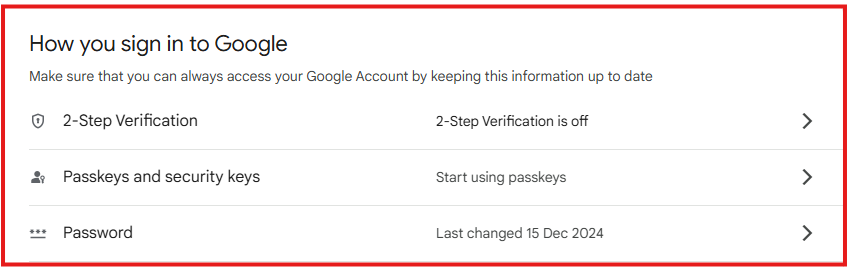
1. Check If Your Account Supports Multi-Factor Authentication
Most major online services, such as email providers, social media platforms, and banking websites, offer MFA. Look for the security settings or account settings section to see if MFA is available.
2. Choose Your Preferred MFA Method
Different services offer various MFA options, including:
- One-Time Passwords (OTP) via SMS or email.
- Authenticator Apps like Google Authenticator or Microsoft Authenticator.
- Biometric Authentication (fingerprint or facial recognition).
- Security Keys such as YubiKey for advanced protection.
Select the method that best suits your needs.
3. Enable MFA in Your Account Settings
Once you choose an MFA method:
- Navigate to the Security or Login Settings of your account.
- Look for the Multi-Factor Authentication or Two-Step Verification option.
- Click Enable and follow the setup instructions.
4. Set Up an Authenticator App (Recommended Method)
For stronger security, use an authenticator app:
- Download Google Authenticator, Microsoft Authenticator, or Authy.
- Scan the QR code provided by your online account.
- Enter the generated code to verify and complete the setup.
5. Save Backup Codes
Most services provide backup codes during the MFA setup process. These are essential in case you lose access to your authentication method. Save them in a secure place.
6. Test Your Multi-Factor Authentication
Before logging out, test the MFA setup:
- Log out and attempt to sign in again.
- Enter your password and complete the second verification step.
- Ensure you can access your account with MFA enabled.
7. Enable MFA on All Critical Accounts
For maximum security, enable MFA on:
- Email accounts (Gmail, Outlook, Yahoo)
- Social media (Facebook, Twitter, Instagram)
- Banking and financial accounts
- Cloud storage and work accounts
Final Thoughts
Setting up multi-factor authentication (MFA) is a simple but powerful way to protect your personal and financial information. By enabling MFA on all critical accounts, you significantly reduce the risk of cyberattacks and unauthorized access.
Comparing MFA Methods: Which One is the Most Secure?
Not all multi-factor authentication (MFA) methods provide the same level of security. While any form of MFA is better than relying on a password alone, some methods offer stronger protection against cyber threats. In this guide, we compare different MFA methods to determine which one is the most secure.
1. SMS-Based One-Time Passwords (OTP)
📌 How It Works: A temporary code is sent to your phone via SMS, which you enter to complete login.
✅ Pros:
- Easy to use and widely supported.
- No extra app or device required.
❌ Cons:
- Vulnerable to SIM swapping attacks, where hackers hijack your phone number.
- Can be intercepted through phishing or malware.
2. Email-Based Authentication
📌 How It Works: A verification link or code is sent to your email.
✅ Pros:
- Convenient and easy to access.
- Works on any device with email access.
❌ Cons:
- If your email account is compromised, attackers can bypass MFA.
- Not as secure as app-based authentication.
3. Authenticator Apps (TOTP – Time-Based One-Time Passwords)
📌 How It Works: Apps like Google Authenticator, Microsoft Authenticator, and Authy generate time-sensitive codes that must be entered during login.
✅ Pros:
- More secure than SMS or email-based methods.
- Works offline, reducing hacking risks.
❌ Cons:
- If you lose your phone, recovery can be difficult without backup codes.
4. Push Notification-Based Authentication
📌 How It Works: Instead of entering a code, users receive a push notification on a trusted device and simply tap “Approve” or “Deny.”
✅ Pros:
- Resistant to phishing attacks since users don’t enter a code.
- Quick and user-friendly.
❌ Cons:
- Requires internet access.
- Can be exploited through push fatigue attacks (hackers spam approval requests until a user mistakenly approves one).
5. Biometric Authentication (Fingerprint, Face Recognition, Iris Scan)
📌 How It Works: Uses physical traits like fingerprints, facial recognition, or iris scans for authentication.
✅ Pros:
- Fast and convenient.
- Hard to duplicate, making it more secure than passwords.
❌ Cons:
- Can be bypassed with high-quality images or deepfake technology.
- If compromised, biometric data cannot be changed like a password.
6. Security Keys (Hardware Tokens – FIDO2, YubiKey, Titan Key)
📌 How It Works: Users insert or tap a physical security key (USB, NFC, or Bluetooth) to authenticate login.
✅ Pros:
- The most secure MFA method available.
- Immune to phishing, SIM swapping, and malware attacks.
❌ Cons:
- Requires carrying a physical device.
- Can be lost, requiring a backup method.
Which MFA Method is the Most Secure?
Here’s a security ranking of MFA methods from least to most secure:
- Least Secure: SMS-Based OTP
- Email-Based Authentication
- Push Notifications
- Authenticator Apps (TOTP)
- Biometric Authentication
- Most Secure: Security Keys (FIDO2, YubiKey)
For maximum security, experts recommend using hardware security keys (FIDO2) or an authenticator app (TOTP) as your primary MFA method. Avoid SMS-based MFA if possible, as it is the easiest to hack.
Final Thoughts
While all multi-factor authentication (MFA) methods improve security, choosing the right one depends on your needs. For everyday users, an authenticator app provides a good balance between security and convenience. For businesses and high-risk accounts, a security key offers the best protection.
Pros and Cons of Using Multi-Factor Authentication
Multi-factor authentication (MFA) is a powerful security feature that helps protect online accounts by requiring multiple verification methods. While MFA significantly enhances security, it also comes with some drawbacks. In this article, we will explore the pros and cons of using multi-factor authentication to help you determine if it’s the right choice for your needs.
Pros of Multi-Factor Authentication
1. Stronger Security Against Cyber Threats
MFA adds an extra layer of protection, making it much harder for hackers to access your accounts, even if they steal your password.
✅ Why It’s Important:
- Protects against phishing attacks.
- Reduces the risk of unauthorized access.
2. Protection from Password Theft
Many people reuse passwords across multiple sites. If one password is leaked in a data breach, hackers can access multiple accounts. MFA prevents this by requiring a second authentication factor.
✅ Why It’s Important:
- Stops attackers from using stolen passwords.
- Adds extra protection for sensitive data.
3. Multiple Authentication Options
MFA provides different authentication methods, including:
- One-time passwords (OTP) via SMS or email.
- Authenticator apps like Google Authenticator or Microsoft Authenticator.
- Biometric authentication (fingerprint, face recognition).
- Security keys (YubiKey, FIDO2).
✅ Why It’s Important:
- Users can choose a method that fits their needs.
- Higher flexibility and convenience.
4. Helps Prevent Unauthorized Logins
Even if a hacker tries to log in from an unknown device, MFA will require additional verification before granting access.
✅ Why It’s Important:
- Stops unauthorized login attempts.
- Provides alerts when someone tries to access your account.
Cons of Multi-Factor Authentication
1. Inconvenience and Extra Steps
MFA adds an extra step to the login process, which may be inconvenient for users who prefer quick access to their accounts.
❌ Challenges:
- Takes extra time to log in.
- Some methods require carrying a physical device (e.g., security keys).
2. Risk of Losing Access to Accounts
If you lose access to your authentication method (e.g., your phone with an authenticator app or security key), regaining access can be difficult.
❌ Challenges:
- Users may get locked out if they don’t have backup codes.
- Recovery processes can be time-consuming.
3. Vulnerability to Certain Attacks
While MFA greatly improves security, some methods (like SMS-based MFA) can still be compromised through SIM-swapping attacks or phishing scams.
❌ Challenges:
- SMS-based MFA is vulnerable to hacking.
- Users may fall for phishing attempts that trick them into revealing MFA codes.
4. Not All Services Support MFA
Although many major platforms offer MFA, some websites and applications still do not support it, leaving users with limited protection options.
❌ Challenges:
- Users cannot enable MFA on every account.
- Some platforms only offer weak MFA options like SMS-based verification.
Final Thoughts
Despite some drawbacks, the benefits of multi-factor authentication (MFA) far outweigh the inconveniences. Enabling MFA on your critical accounts adds a strong layer of security that can prevent cyber threats and unauthorized access.
For the best protection, use strong MFA methods like authenticator apps or security keys instead of SMS-based authentication.
Conclusion: Why You Should Enable Multi-Factor Authentication Today
In today’s digital world, multi-factor authentication (MFA) is one of the most effective ways to protect your personal and professional information from cyber threats. With the rise of data breaches, phishing attacks, and increasingly sophisticated hacking techniques, relying on just a password is no longer sufficient to keep your accounts secure.
Enabling MFA provides an extra layer of protection, making it much harder for hackers to gain unauthorized access, even if they manage to steal your password. Whether you’re protecting your email, social media, banking, or cloud storage accounts, MFA adds that crucial barrier against cyberattacks.
Why Enable MFA Today?
- Enhanced Security: MFA provides multiple verification factors, which significantly reduce the risk of unauthorized access.
- Protection Against Password Theft: Even if your password is compromised, MFA ensures that a second authentication factor is needed to gain access.
- Easy Setup: Most online services offer straightforward MFA setup options, including apps, push notifications, and biometric methods.
- Peace of Mind: Knowing that your accounts are secured with multiple layers of defense offers peace of mind and reduces the stress of potential cyber threats.
Final Word
Don’t wait for a cyberattack or data breach to occur—enable multi-factor authentication today to safeguard your accounts. It’s an easy, effective step you can take to improve your online security and protect sensitive data from hackers. By adding that extra layer of defense, you’re ensuring that your information stays protected in an increasingly vulnerable digital world.
Take action now—enable MFA on all of your critical accounts to stay one step ahead of cybercriminals!